Here's the list of things I do when troubleshooting a slow computer:
1) Run a malwarebytes scan and remove anything found
2) Install all applicable driver updates
3) Run "sfc /scannow" from an elevated command prompt
4) Install all applicable Windows updates
5) Install all applicable Office updates, if installed separately (true for some versions of Office 2016)
6) Check amount of free disk space (ideally at least 20 GB free)
7) Check for adware/crapware that is installed. Remove by normal add/remove programs
8) Check CPU usage and disk usage for conditions above 99%
Showing posts with label malware. Show all posts
Showing posts with label malware. Show all posts
Friday, August 11, 2017
Slow computer troubleshooting
Labels:
adware,
antivirus,
malware,
scannow,
sfc,
sfc /scannow,
slow,
slow computer
Friday, November 14, 2014
Internet Explorer proxy settings won't change - "some settings are managed by system adminsitrator"
Credit for this solution belongs here:
I came across a computer with a malware infection that had its Internet Explorer proxy settings configured, but I couldn't remove the proxy settings. When I went to internet properties, it said "some settings are managed by system adminsitrator"
This computer was not part of a domain and had nothing set in local policies. The fix was to change the value for ProxySettingsPerUser from 0 to 1 in the registry here:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings -> ProxySettingsPerUser
I came across a computer with a malware infection that had its Internet Explorer proxy settings configured, but I couldn't remove the proxy settings. When I went to internet properties, it said "some settings are managed by system adminsitrator"
This computer was not part of a domain and had nothing set in local policies. The fix was to change the value for ProxySettingsPerUser from 0 to 1 in the registry here:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\CurrentVersion\Internet Settings -> ProxySettingsPerUser
Thursday, June 30, 2011
removing XP Antivirus 2012
I've found XP antivirus 2012 to be easier to remove than most other of the fakealert viruses.
With XP antivirus 2012, you can use control-alt-delete to end task. Then run an rkill. Then run quick malwarebytes scan and remove everything, but don't reboot. Then run a full malwarebytes scan. You may find that the virus restarts even after an rkill after 3 or 4 minutes. Just close the program again and run an rkill and let the quick malwarebytes scan to keep the virus from restarting. Then run the full scan to completely get rid of the virus.
Labels:
2012,
fake alert,
fakealert,
malware,
XP antivirus 2012
Friday, May 6, 2011
using combofix in safe mode with command prompt
I was faced with a fakealert virus yesterday that existed in safe mode also, which made cleaning it very difficult. I used the command prompt method I used a couple weeks ago to clean it. Luckily, I was on a network - not sure I would have been able to do this on a stand alone computer. Here were my steps:
[on the virus affected machine]
boot into safe mode with networking
log in as a domain admin
create new local administrator (on the chance that I didn't know the local admin password)
[from another machine in the network that is not infected]
from another machine on the network logged in as a domain admin
go to \\10.0.0.54\c$ (affected computer drive)
create a new folder on the root of C called malware
download newest version of combofix and copy it to \\10.0.0.54\c$\malware
[on the virus affected machine]
reboot into safe mode with command prompt
log in as local administrator
run c:\malware\combofix.exe
You won't be able to install the recovery console, but in the two times I've tried this, it hasn't been a problem.
Labels:
combofix,
command prompt,
fakealert,
malware,
safe mode
Monday, April 11, 2011
handling windows restore fakealert virus
Today, I dealt with another one of those fakealert viruses. This one was called windows restore. I had to take a couple minor extra steps. I booted to safe mode with networking. I found that the virus had removed the DNS servers (which had been statically set on this computer). I added those back and was then able to download malwarebytes. One thing that was super weird was that it had hidden all files and folders. I ran start -> run -> iexplore to start IE, but I also unhid all files.
After running malwarebytes and removing the virus, I found that all files were still hidden. I ran this from a DOS prompt to remedy that:
attrib *.* -s -h /s /d
And things were back to normal.
Of course I ran these instructions to clean the virus:
Labels:
fake alert,
fakealert,
malware,
malwarebytes,
windows restore
Monday, November 29, 2010
cleaning spyware/malware in safe mode using malwarebytes
To get the most surefire cleaning from malwarebytes to remove malware from an infected computer, I recommend running malwarebytes in safe mode. This tutorial will guide you trough booting into safe mode with networking and then running malwarebytes.


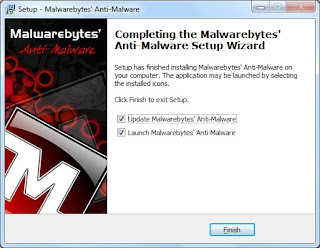
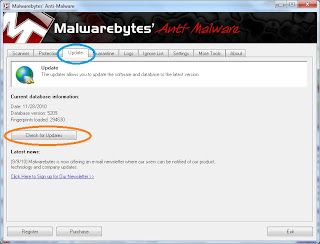
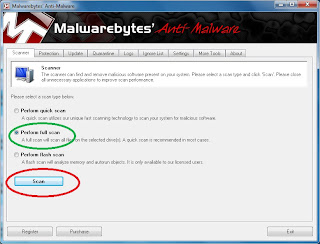
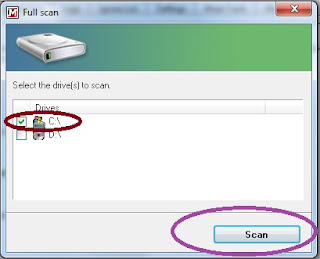
Step 1:
The first thing you need to do is shut down your computer. Do this normally using Start -> Shutdown. Instead of choosing restart, you should shut the computer all the way down.
Step 2:
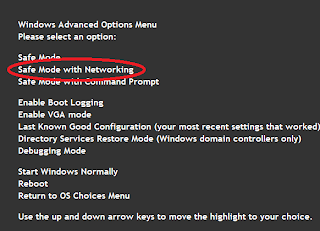
Turn the computer on and, wait approximately one second and then start pressing the F8 key about 2 times per second. There is a brief time window early during the booting process when we can reach the advanced startup menu. It's hard to see, so we just press F8 repaeatedly until we see it.

Step 3:
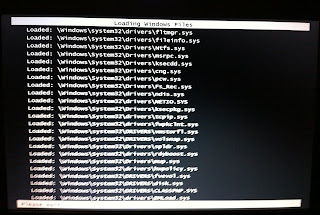
Choose Safe Mode with Networking in the advanced startup menu. Afterward, you'll get a bunch of diagnostic info on the screen about what is loading. This is normal. You can ignore it. (If you don't get the advanced start menu, your computer will boot normally. Shut down again and start on step 1).


Step 4:
Log in normally.
Step 5:
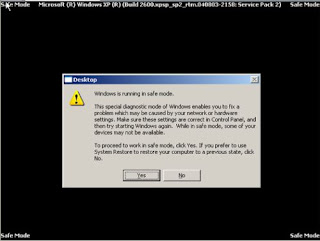
If you are asked if you want to continue in safe mode or run a system restore , hit YES - so that you continue to work in safe mode.

Step 6:
If you have already downloaded and installed Malwarebytes, run it now and skip to step 8. If not, go to step 7.

Step 7:
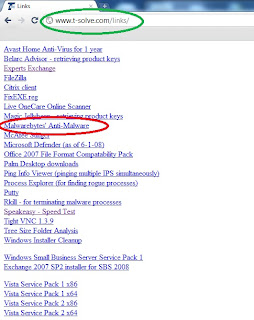
You can download and install Malwareware bytes from www.t-solve.com/links. Download and install Malwarebytes (you can accept all the defaults).


Step 8:
With the software open, run an update by going to the update tab and then pressing check for updates.

Go to the scanner tab. Choose a full scan and press scan. Then in the next box, choose the C drive and hit scan.


This scan will take anywhere from 30 minutes to 2 hours depending on the speed of your computer and the number of files that Malwarebytes needs to scan. With most computers that are a year old or newer, a scan will usually take 45 to 60 minutes.
Step 9:
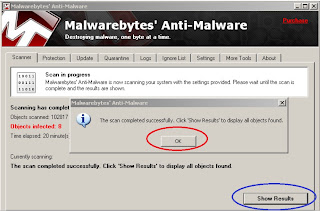
With the scan complete, you'll see that it found objects infected. At this point, click OK and then Show Results.

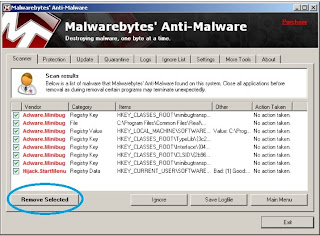
Step 10:
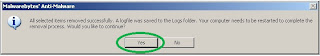
Click on "remove selected" on the next window that comes up. Then close text window that comes up next and click YES to restart your computer (sometimes you are not prompted to restart your computer - that's ok - you'll want to restart anyway to get out of safe mode).



After the reboot, log in normally, and you should be clean from all the malware that infected you before.
Tuesday, March 9, 2010
malware removal tools
The fakealert malware viruses are everywhere. I've managed to rid most of them with just two tools:
rkill - to terminate the running processes
Malwarebytes - to remove the infections
For just about every fakealert virus, I put rkill.com and mbam.exe (links above) on a flash drive and then run rkill.com on the infected computer. Then I run Malwarebytes full scan and then remove whatever it suggests.
---
The other day, I came across a machine with different symptoms - just in time debugging kept coming up over and over again. I fixed it with combofix, but here's also another suggested tool that I didn't have to use:
Combofix
Dr. Web CureIt
So far, I've fixed every infection I've found using some combination of these tools. I wonder when the antivirus vendors will ever get a hold on this. It's been over a year that these types of viruses have been in the wild.
rkill - to terminate the running processes
Malwarebytes - to remove the infections
For just about every fakealert virus, I put rkill.com and mbam.exe (links above) on a flash drive and then run rkill.com on the infected computer. Then I run Malwarebytes full scan and then remove whatever it suggests.
---
The other day, I came across a machine with different symptoms - just in time debugging kept coming up over and over again. I fixed it with combofix, but here's also another suggested tool that I didn't have to use:
Combofix
Dr. Web CureIt
So far, I've fixed every infection I've found using some combination of these tools. I wonder when the antivirus vendors will ever get a hold on this. It's been over a year that these types of viruses have been in the wild.
Tuesday, September 29, 2009
EXE files disassciated
Today, after running the anti-malware program here:
http://www.bleepingcomputer.com/virus-removal/remove-windows-police-pro
I'm not sure if was the malware itself, Windows Police Pro, or the fix - but afterward, no EXE files would run. Not Word, not regedit, not Windows XP SP 3. I fixed it with this:
http://windowsxp.mvps.org/exefile.htm
http://www.bleepingcomputer.com/virus-removal/remove-windows-police-pro
I'm not sure if was the malware itself, Windows Police Pro, or the fix - but afterward, no EXE files would run. Not Word, not regedit, not Windows XP SP 3. I fixed it with this:
http://windowsxp.mvps.org/exefile.htm
Labels:
EXE,
fake alert,
malware,
Police,
Windows Police Pro
removing fake alert malware
Found some good resources for removing some of the fake alert malware out there.
http://www.bleepingcomputer.com/virus-removal/remove-windows-antivirus-pro
http://www.bleepingcomputer.com/virus-removal/remove-windows-police-pro
Who knows why Symantec, McAfee, and Avast are so far behind the ball on dealing with these fake alert things - but at least there's an automated option out there.
Even if there is a new piece of fake alert malware out there, I generally have good success trying a system restore first and then if not (usually because it deleted all the restore points) then you can usually go into safe mode and delete the registry keys, EXEs, DLLs, and stuff.
http://www.bleepingcomputer.com/virus-removal/remove-windows-antivirus-pro
http://www.bleepingcomputer.com/virus-removal/remove-windows-police-pro
Who knows why Symantec, McAfee, and Avast are so far behind the ball on dealing with these fake alert things - but at least there's an automated option out there.
Even if there is a new piece of fake alert malware out there, I generally have good success trying a system restore first and then if not (usually because it deleted all the restore points) then you can usually go into safe mode and delete the registry keys, EXEs, DLLs, and stuff.
Labels:
fake alert,
malware,
msconfig,
regedit,
safe mode,
system restore,
virus
Monday, October 6, 2008
fix for WinXP2008 virus and xpsecuritycenter
I haven't tested this yet honestly - but an associate gave me this batch file saying that it would clean out the WinXP2008 virus if you run it in safe mode. True? Not sure yet.
Labels:
malware,
virus,
wallpaper,
winxp2008,
xpsecuritycenter
Saturday, August 23, 2008
dealing with malware that alters display properties
Over the past two weeks, I've seen three pieces of malware that alter the display properties in Windows XP. In each instance, I was able to get rid of malware with Symantec AV 10.1 and then Avast Antivirus 4.8. But the display properties remained changed.
In one instance, it created a strange screen saver that emulated a BSOD. In another instance, it changed the wallpaper to a spyware warning. But the weird thing is that if you go to the display properties, the necessary tabs you need to reverse those problems are gone.
Best course of action is to use this wallpaper hijacker remover:
http://www.majorgeeks.com/Wallpaper_Hijack_Remover_d4816.html
Here is what an altered wallpaper looks like:

In one instance, it created a strange screen saver that emulated a BSOD. In another instance, it changed the wallpaper to a spyware warning. But the weird thing is that if you go to the display properties, the necessary tabs you need to reverse those problems are gone.
Best course of action is to use this wallpaper hijacker remover:
http://www.majorgeeks.com/Wallpaper_Hijack_Remover_d4816.html
Here is what an altered wallpaper looks like:

Labels:
hijacked,
hijacker,
malware,
screen saver,
wallpaper
Subscribe to:
Posts (Atom)
